

Hello and welcome to our Linux basics course, the idea of this course is provide to you the enough knowledge to move like a fish in Linux
The field of Information Technology (IT) is full of opportunities. For individuals who wish to pursue a career in IT, one of the biggest challenges can be deciding how to get started. People are often motivated to learn new skills that will enable them to pursue bigger and better opportunities in their personal and professional lives. Learning a new skill takes time and discipline, but with the right motivation, it doesn’t have to be painful. In this section, we will discuss why the time and effort you invest in learning Linux will benefit you; remember, everyone working in IT had to start somewhere
it is highly recommend to have one of the next tools to execute the commands
The Linux command-line: is a text-based interface that accepts commands that you type into it.
Git-bash: is an application for Microsoft Windows environments which provides an emulation layer for Git command line experience.
WSL2: Windows Subsystem for Linux lets developers run a GNU/Linux environment.
PuTTY: is a free and open-sourced terminal emulator, serial console and network file transfer application.
A command is a software program that when executed on CLI(command-line interface), performs an action on the computer. When you type in a command, a process is run by the operating system that can read input, manipulate data and produce output. A command runs a process on the operating system, which then causes the computer to perform a job
An argument can be used to specify something for the command to act upon. The LS command can be given the name of a directory as an argument, and it will list the contents of that directory.
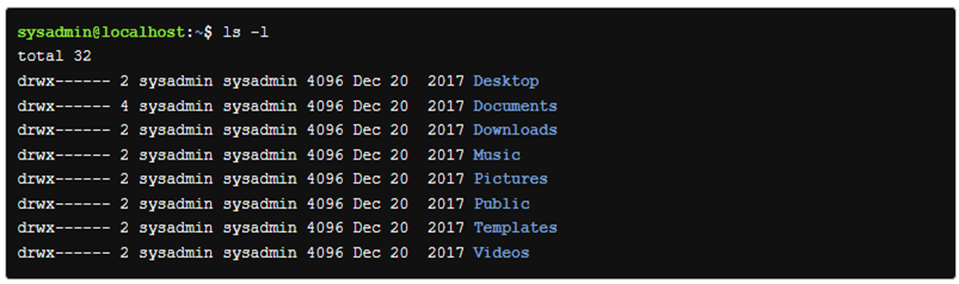
Options can be used to alter the behavior of a command, in the previous slide, the ls command was used to list the contents of a directory. In the following, the –l option is provided to the ls command, which results in a “long display” output, meaning the output gives ore information about each of the files listed:
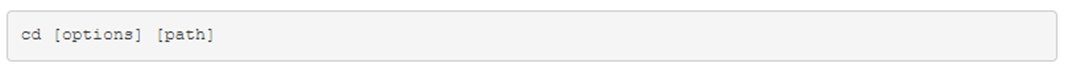
In order to discover where you are working currently located within the filesystem, the PWD command can be used. The PWD command prints the working directory, your current location within the filesystem:
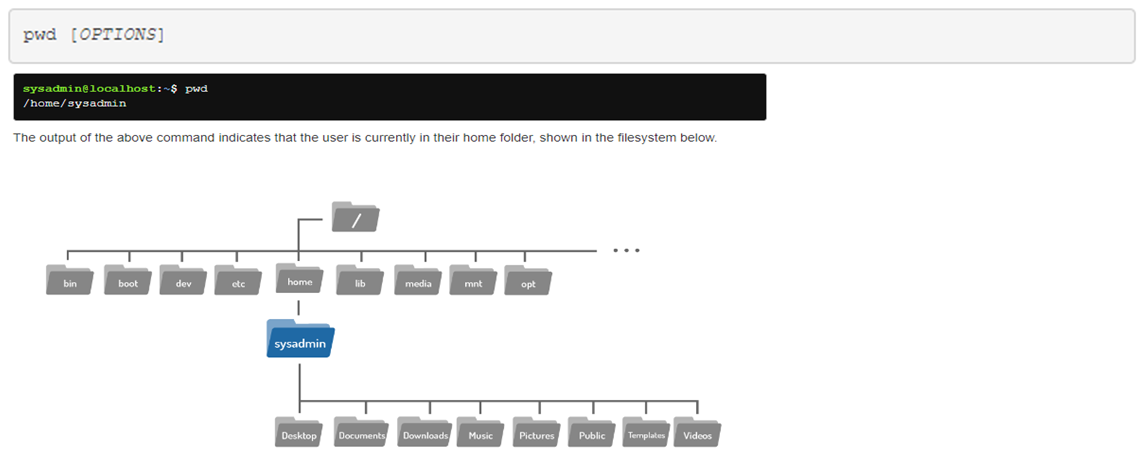
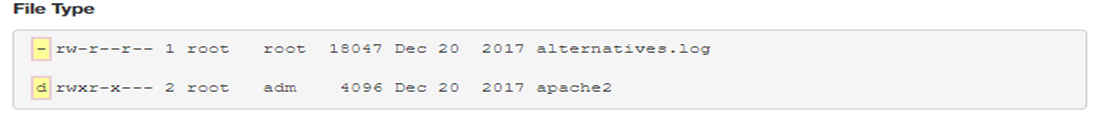
Files are used to store data such as text, graphics and programs. Directories are a type of file used to store other files-they provide a hierarchical organizational structure. The image shows an abbreviated version of the filesystem structure on the virtual machines
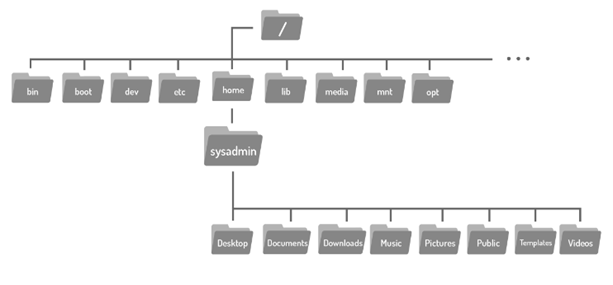
To navigate the filesystem structure, use the cd (change directory) command to change directories
If we look back at the graphic, we will see the Documents directory is located within the home directory, where you are currently located. To move to the Documents directory, we use it as argument to the cd command
An absolute path allows you to specify the exact location of a directory. It always starts at the root directory, therefore it always begins with the / character. The path to the home directory /home/sysadmins is an absolute path. The path begins at the root/directory, moves into the home directory, and then into the sysadmin directory.
A relative path gives directions to a file relative to your current location in the filesystem. Relative paths do not start with the / character, they start with the name of a directory
| Shortcuts | |
| The .. Characters | Regardless of which directory you are in, .. always represents one directory higher relative to the current directory, sometimes referred to as the parent directory. To move from the Art directory back to the School directory |
|
The . Character |
Regardless of which directory you are in, the . character always represents your current directory. For the cd this shortcut is not very useful, but it will come in handy for commands covered in subsequent sections |
|
The ~ Character |
The home directory of the current user is represented by the ~ character. As stated above, you always begin as the sysadmin user, whose home is located at /home/sysadmin. To return to your home directory at any time execute the following command |
The ls command is used to list the contents of a directory. You’ve already seen it used a few times before in examples but this time will dig into details provided by this command
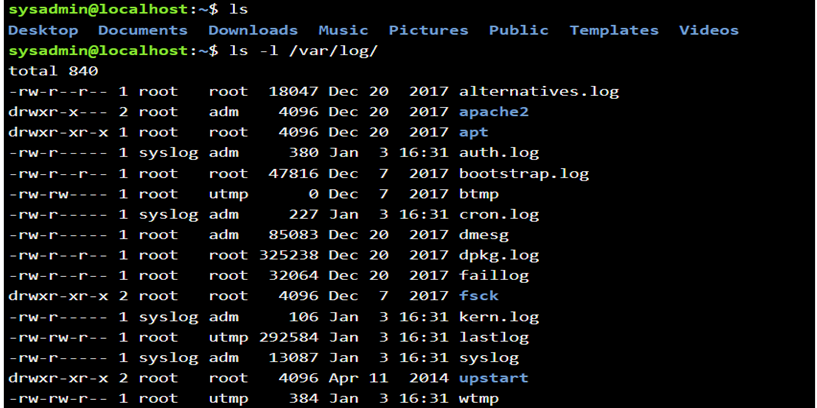
so, let see an example of two outputs:
| Permision | example |
| Permissions | |
| Hard Link Count | 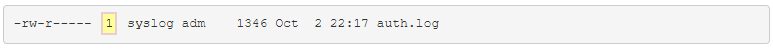 |
| User Owner | 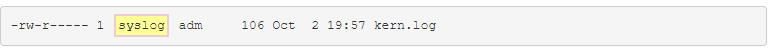 |
| Group Owner | |
| File Size | |
| Timestamp | |
| Filename | 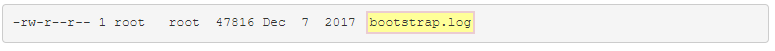 |
By default, the output of the ls command is sorted alphabetically by filename. It can sort by another method as well. The options in the next examples will be combined with the -l option so the relevant details of the files are displayed.
| Option | What does |
| -t | will sort the file by timestamp |
| -S | will sort the files by file size(pay attention here, the S is capital) |
| -r | will reverse the order of any type of sort(if we use only the -r option it will list the files in reverse alphabetical order) |
There are many Linux commands which deal with sensitive information like passwords, syste hardware, or otherwise operate under other exceptional circumstances. Preventing regular users from executing these commands helps to protect the system. Logging in as the root user provides administrative access, allowing for the execution of some of the priviliged commands.
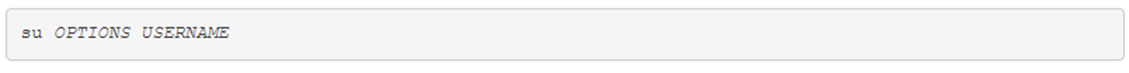
The su command allows you to temporarily act as different user. It does this by creating a new shell. The shell is simply a text input console that lets you type in commands. By default, if a user account is not specified, the su command will open a new shell as the root user, which provides administrative privileges.
sudo commandThis command allows a user to execute a command as another user without creating a new shell. Instead to execute a command with administrative privileges, use it as an argument to the sudo command. Like the su command, the sudo command assumes by default the root user account should be used to execute commands
Hint: You can use the sudo command to switch to other user accounts as well. To specify a different user account use the -u option.
Permissions determine the ways different users can interact with a file or directory. The output includes permissions information when listing a file with the ls -l command. Let is check the next example
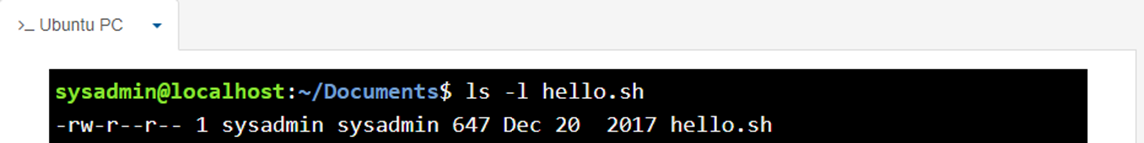
File type field ![]()
The first character of this output indicates the type of a file. Recall that if the first character is a -, this is a regular file. if the character was a d, it would be a directory
Permissions Field 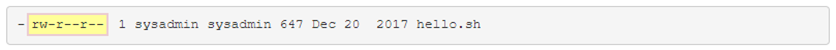
after the file type character, the permissions are displayed. The permissions are broken into three sets of three characters
Owner 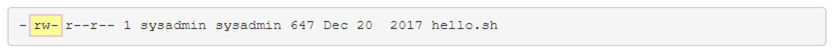
The first set is for the user who owns the file. If your current account is the user owner of the file, then the first set of the three permissions will apply and other permissions have no effect
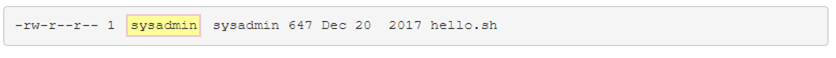
Group 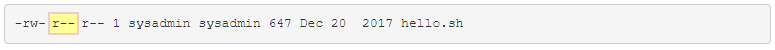
The second set is for the group that owns the file. If your current account is not the user owner of the field and you are a member of the group that owns the file, then the group permissions will apply and the other permissions have no effect.
The group for this file can be determined by the group owner field:
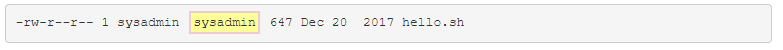
Other 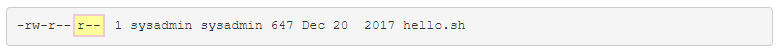
The last set is for everyone els, anyone to whom the first two sets of permissions do not apply to.
Check the next images which explains every character you will find in field permissions

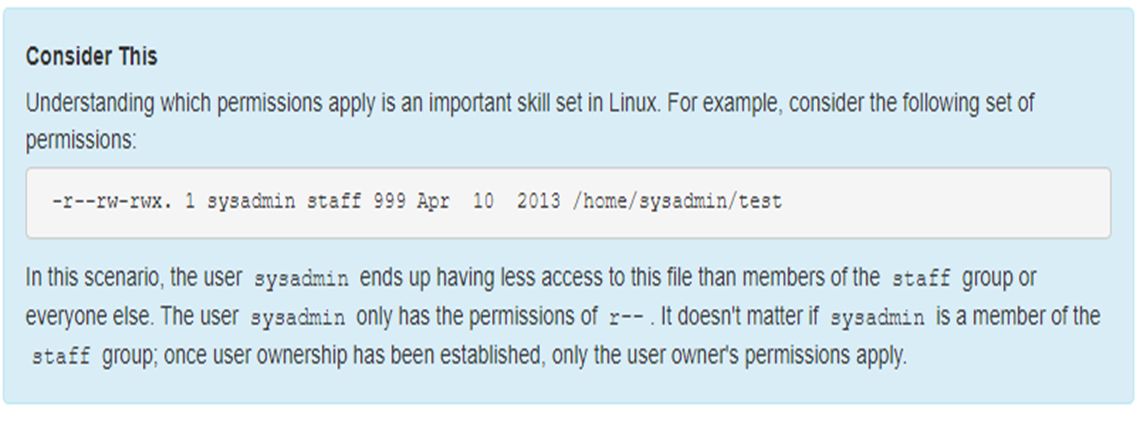
The chmod command is used to change the permissions of a file or directory. In this case, only the user root or the user who owns the file is able to change the permissions of a file.
There are two techniques for changing permissions with chmod command: symbolic and octal. The symbolic method is good for changing one set of permissions at a time, and the octal or numeric method requires knowledge of the octal value of each of the permissions and requires all three sets of permissions(user, group, other) to be especified every time
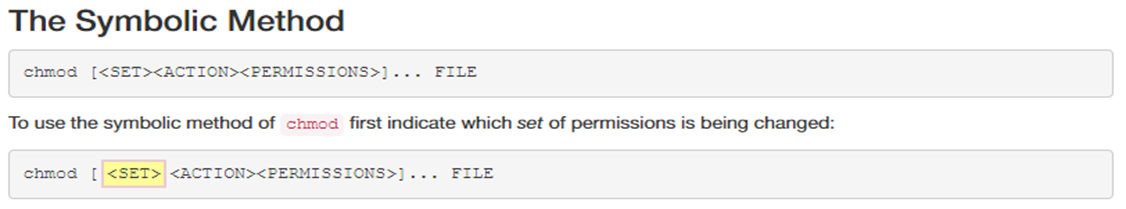
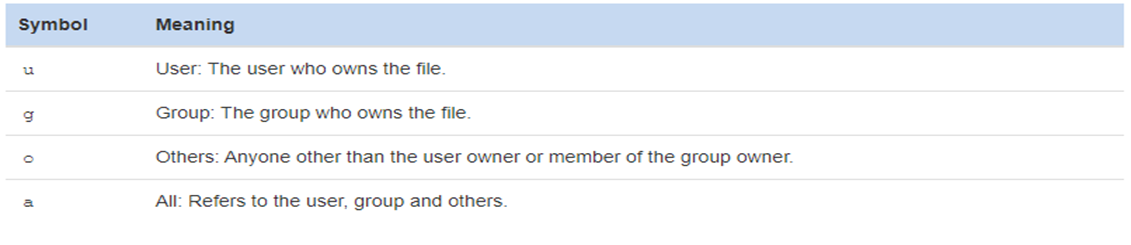
Next, specify an action symbol:
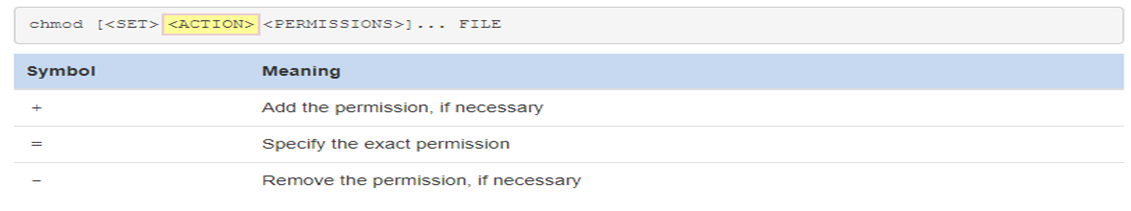
After an action symbol, specify one or more permissions to be acted upon:
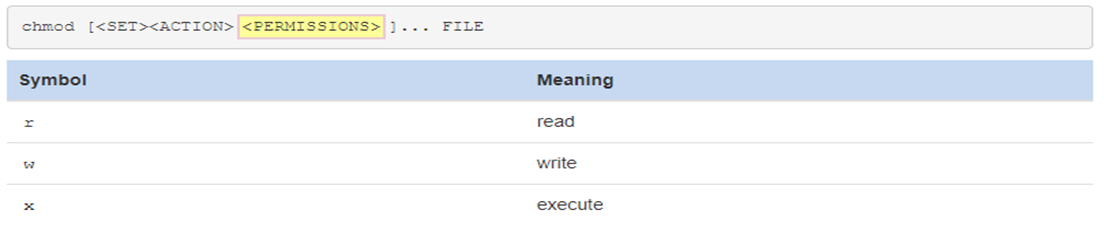
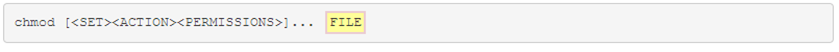
Finally, space and the pathnames for the files to assign those permissions
Initially, the owner of a file is the user who creates it. The chown command is used to change the ownership of files and directories. Changing the user owner requires administrative access. A regular user cannot use this command to change the user owner of a file, even give the ownership of one of their own files to another user.
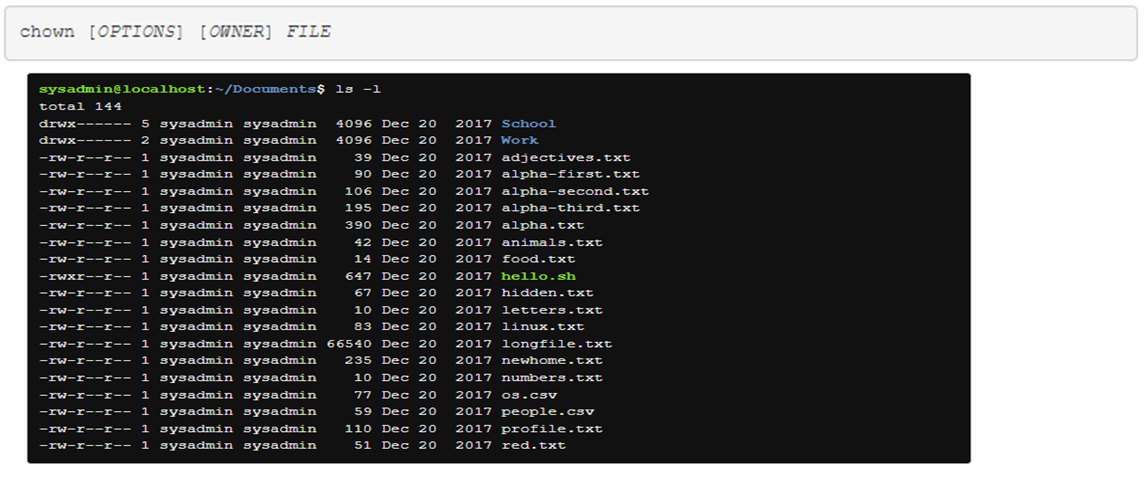
To switch the owner of the hello.sh script to the root user, use root as the first argument and hello.sh as the second
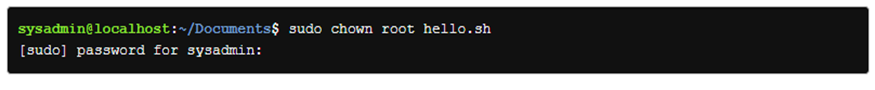
Results:
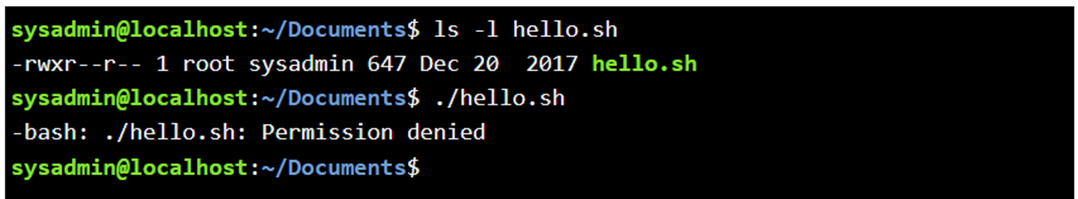
What about if we use sudo after change the owner of the hello.sh
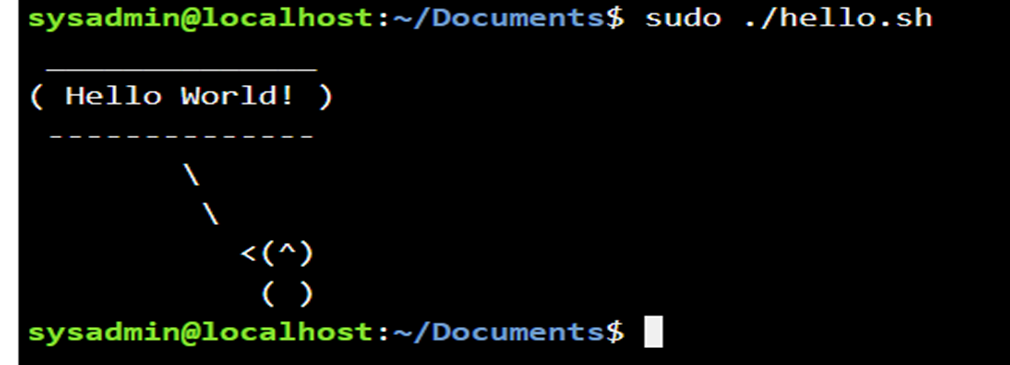
There are a few linux commands available to view the content of files. The cat command, which stands for "concatenate" is often used to quickly view the content of small files
Another way to view the content of files is by using the head and tail commands. These commands are used to view a select number of lines from the top or bottom of a file. Taking a look at a few lines of a file can sometimes be helpful to ensure that the file is the one you want to use. Another reason to preview only the first or last few lines, is because some files, such as system log files are frequently updated with new entries. Similar to the cat command, the head and tail commands use the name of the file you want to view as the argument to the command
Creating copies (cp) of files can be useful for numerous reasons:
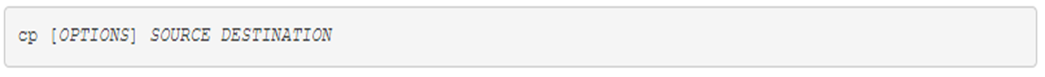
The dd command is a utility for copying files or entire partitions at the bit level
This command has several useful features, including:

The mv command is used to move a file from one location in the filesystem to another.
The command requires at least two arguments, the first one is the source, a path to the file to be moved and the second argument is the destination, a path to where the file will be moved to. The files to be moved are sometimes referred to as the source, and the place where the files are to be placed is called the destination
The rm command is used to delete files and dictionaries, it is important to keep in mind that deleted files and directories, it is important to keep in mind that deleted files and directories do not go into "trash can" as with desktop-oriented operating systems. When a file is deleted with rm command, it is almost always permanently gone
The grep command is a text filter that will search input and return lines which contain a match to give a pattern.
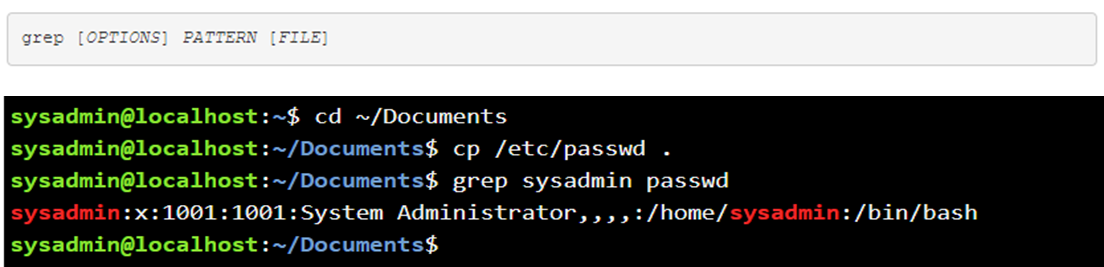
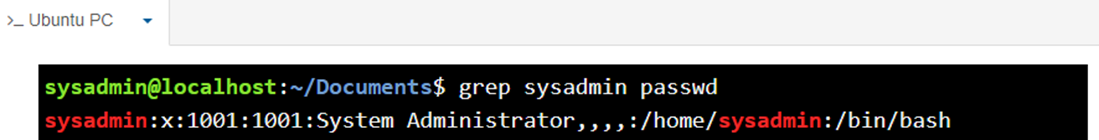
The command above returned the line from passwd which contains the pattern sysadmin
Regular expressions have two common forms: basic and extended. Most commands that use regular expressions can interpret basic regular expressions. However, extended regular expressions are not available for all commands and a command option is typically required for them to work correctly

The following table summarizes the extended regular expressions, which must be used with either the egrep command or the –E option with the grep command

Regular expressions are patterns that only certain commands are able to interpret. Regular expressions can be expanded to match certain sequences of characters in the text. The next examples displayed on this slide will make use of regular expressions to demonstrate their power when used with the grep command. In addition, these examples provide a very visual demonstration of how regular expressions work, the matches are displayed in a red colour
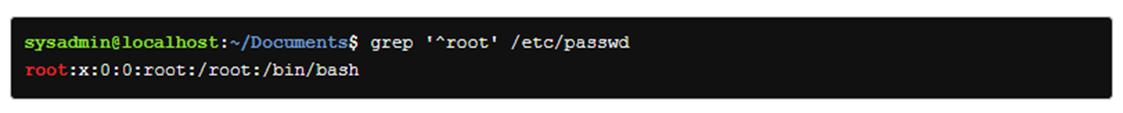
Anchor characters are one of the ways regular expressions can be used to narrow down search results, For example, the pattern root appears many times in the next example:
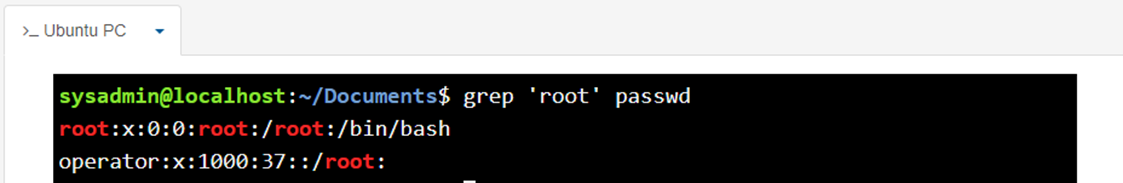
What about if we just want to find the lines where the pattern appears at the beginning?
The shutdown command arranges for the system to be brought down in a safe way. All logged-in users are notified that the system is going down, within the last five minutes leading up to the shutdown, new logins are prevented
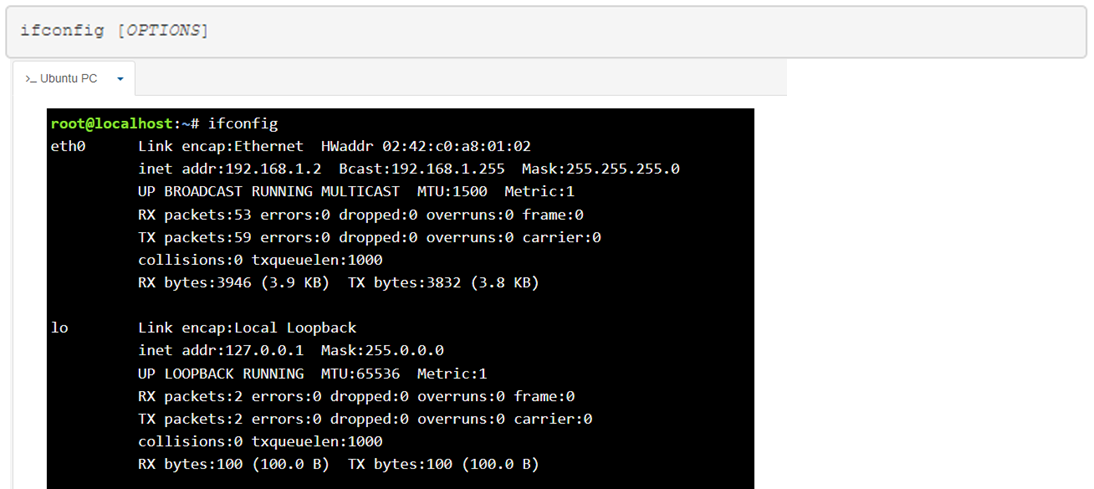
The ifconfig command stands for “interface configuration” and is used to display network configuration information.
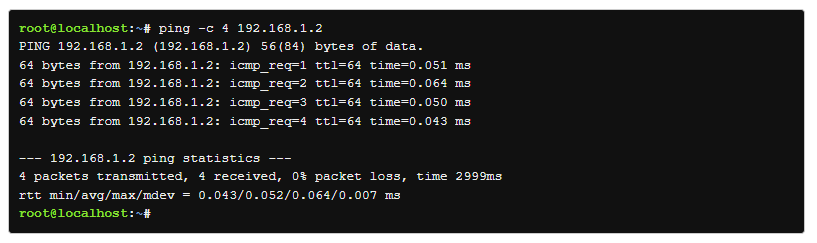
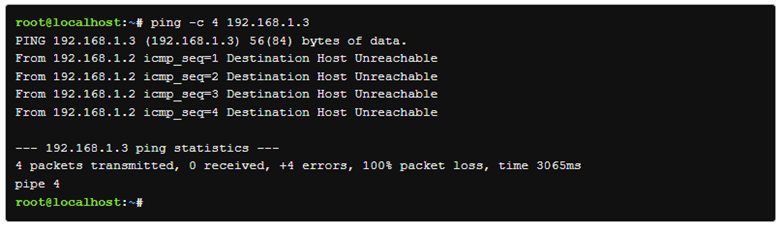
The ping command is used to verify connectivity between two computers. It does this by sending packets to another machine on a network. If the sender receives a response it should be possible to connect to that machine.
if the command is successfull, we will see something like this
if the command fails, we will receive a message staging, destination host unreachable
Running a command results in something called a process. In the Linux operating system, processes are executed with the privileges of the user who executes the command. This allows for processes to be limited to certain capabilities
To list processes, the ps command can be use
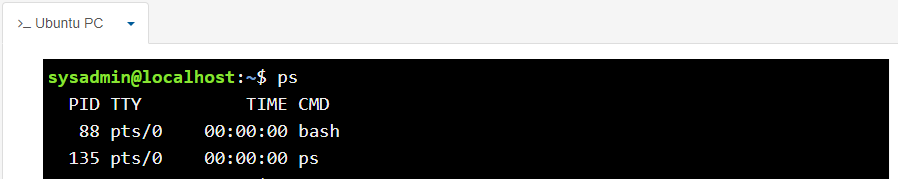
The ps command will display the processes that are running in the current terminal by default. In the example above, the bottom line is the process created by the execution of the ps command. The output includes the following columns of information: PID: The process identifier, which is unique to the process. This information is useful for controlling the process by its ID number. TTY: The name of the terminal where the process is running. This information is useful for distinguishing between different processes that have the same name. TIME: The total amount of processor time used by the process. Typically, this information isn't used by regular users. CMD: The command that started the process.
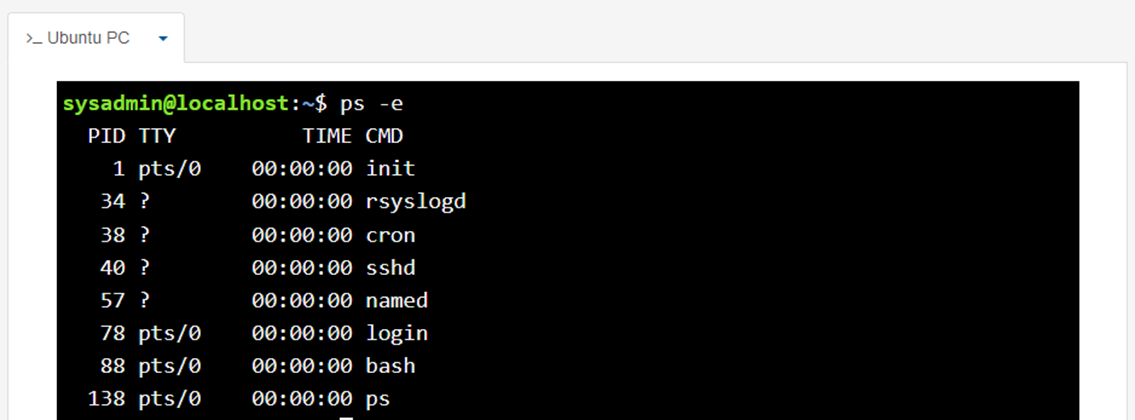
Maybe we want to view more than just processes running in the current terminal, maybe we want to view every process running on the system. The –e option will display every process
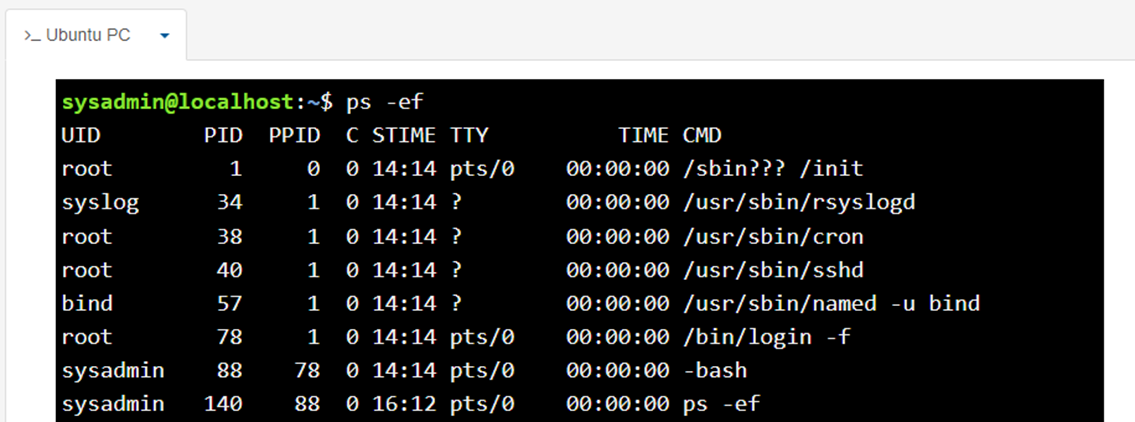
typically, the -f option is also used as it provides more detail in the output of the command, including options and arguments.
Package management is a system by which software can be installed, updated, queried or removed from a filesystem. In Linux, there are many different software package management system, but the two most popular are those from Debian and Red Hat
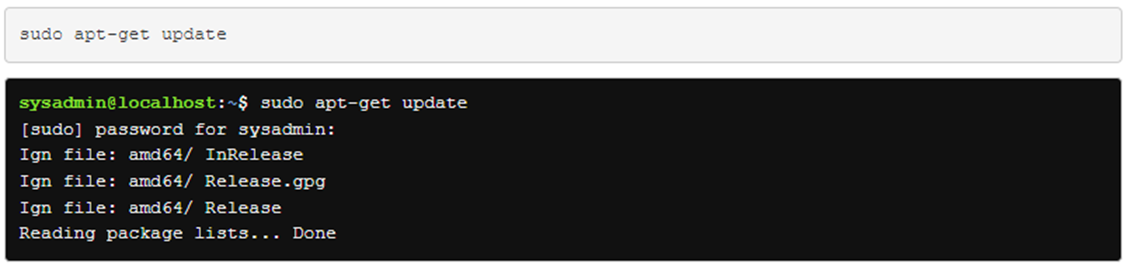
Package files are commonly installed by downloading them directly from repositories located on Internet servers. The Debian repositories contain more than 65,000 different packages of software.
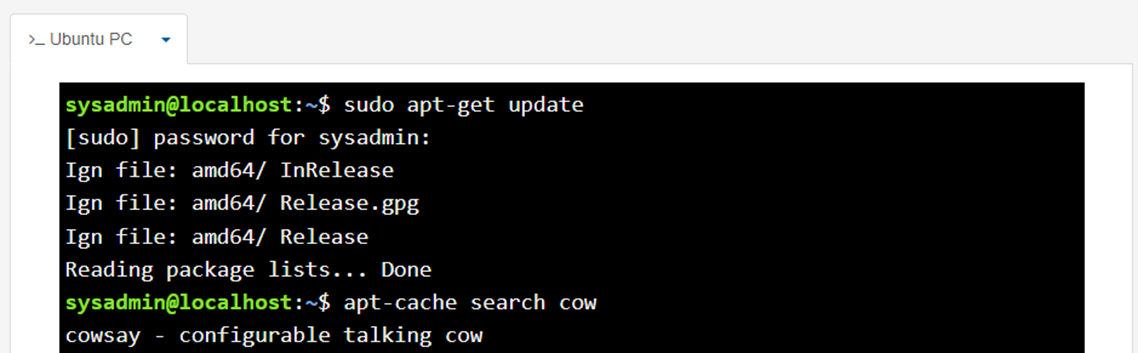
To search for keywords within these packages, you can use the apt-cache search command
The apt-get install command can also update a package, if that package is installed and a newer version is available. If the package is not already on the system, it would be installed; if it is on the system, it would be updated. Updating all packages of the system should be done in two steps. First, update the cache of all packages available with apt-get update. Second, execute the apt-get upgrade command and all packages and dependencies will be updated.
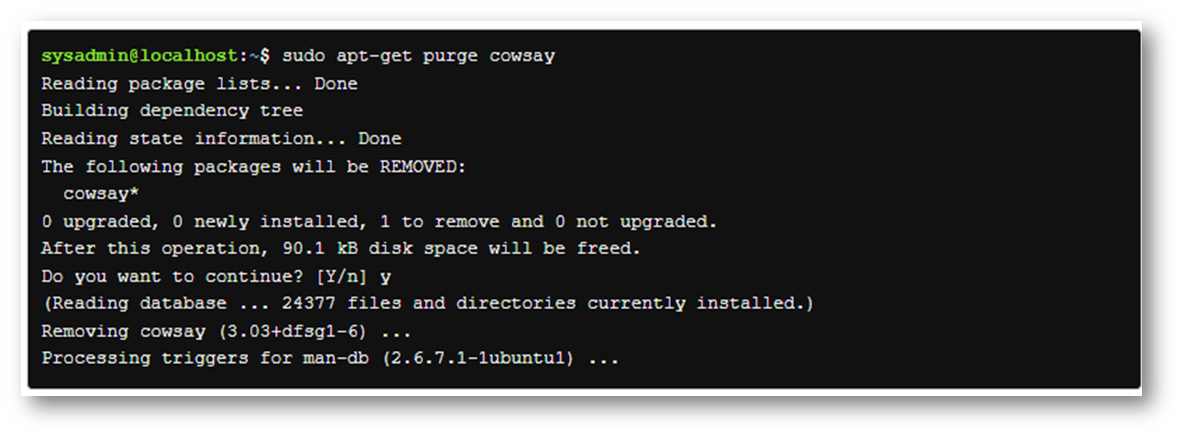
The apt-get command is able to either remove or purge a package. The difference between the two is that purging deletes all package files while removing deletes all but the configuration files for the package
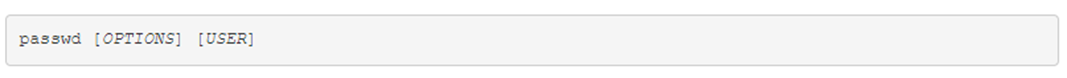
The passwd command is used to update a user’s password. Users can only change their own passwords, whereas the root user can update the password
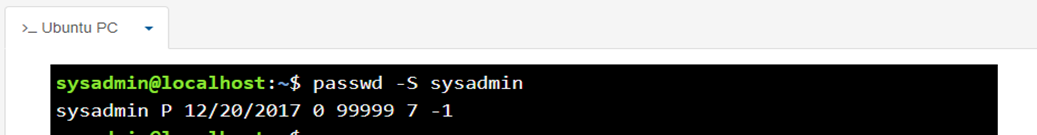
if the user wants to view status information about their password, they can use the -S option:
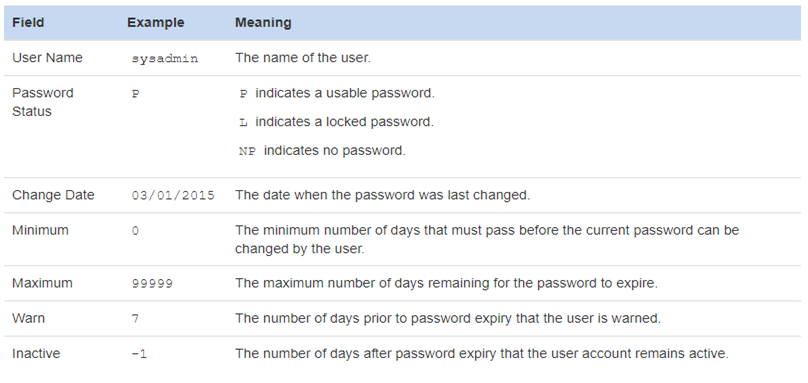
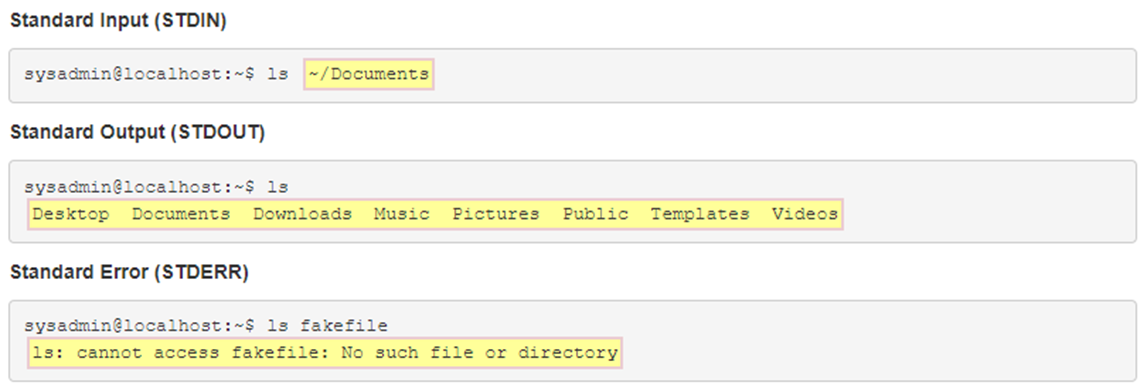
There is a way in Linux to quickly add content to a file using a command line feature called input/output (I/O) redirection. I/O redirection allows for information in the command line to be sent to files, devices, and other commands. The input or output of a command is redirected from its default destination to a different location. I/O redirection is like a series of train tracks, where a switch can be enabled to direct the output of a command on a different track so it goes somewhere else in the shell. In this section, we are writing to files by redirecting the output of a command to a file. When it comes to command input and output there are three paths, or “tracks”. These paths are called file descriptors. The first file descriptor is standard input, abbreviated as STDIN. Standard input is the information the command receives and processes when it is executed, essentially what a user types on the keyboard. The second file descriptor is standard output, abbreviated as STDOUT. Standard output is the information that the command displays, the output of the command. The last file descriptor is standard error, abbreviated as STDERR. STDERR, are the error messages generated by commands that are not correctly executed
Thanks for read our Linux course :).
For any update or advice, please contact me: jesus.vargas@nearshoretechnology.com